The fine-grained password policy that exists in an Active Directory gives it a positive outlook on enhancement through security when there is such differentiation in having particular password needs in different sub-groups of people who share one common domain under one administration umbrella.
Understanding Fine-Grained Password Policies in Active Directory
Fine-grained password policies, or FGPPs, provide for the enforcement of different password and account lockout policies across subsets of users in a single Active Directory domain. This can be useful to implement more strict policies on administrator accounts while more relaxed policies for the general users. Windows Server 2008 brought FGPPs into existence to provide for the presence of more than one password policy within a domain. This will help to make the environment much more secure and compliant
Creating a Fine-Grained Password Policy
To create a fine-grained password policy in Active Directory, you can use the, CionSystems Active Directory Manager Pro(ADMPro), Active Directory Administrative Center (ADAC) or PowerShell.
Using CionSystems Active Directory Manager Pro (ADMPro)
- Login to Active Directory Manager Pro (ADMPro)
- Click on Password, and Fine grained password policy
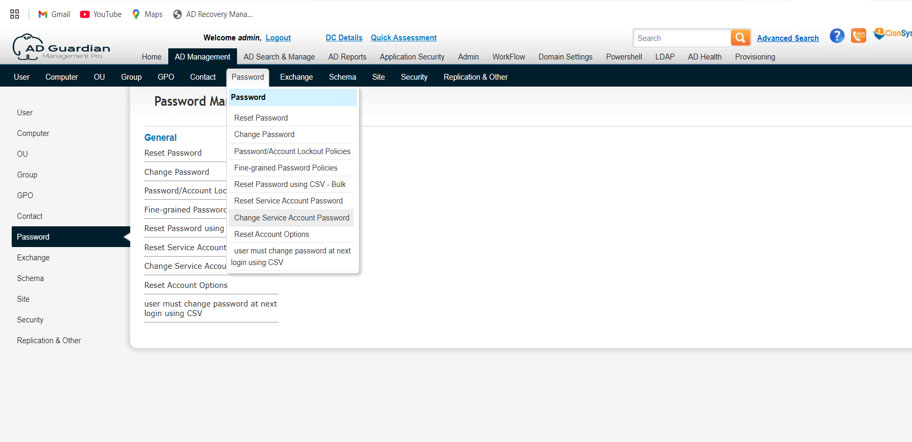
- Click on Create
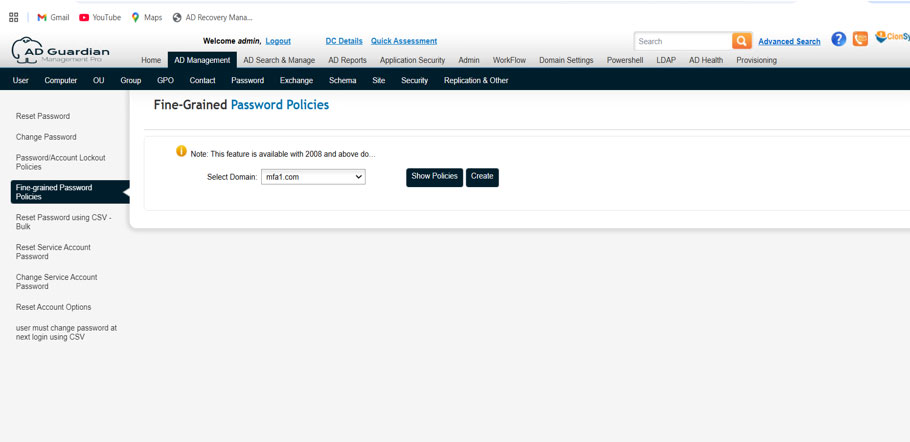
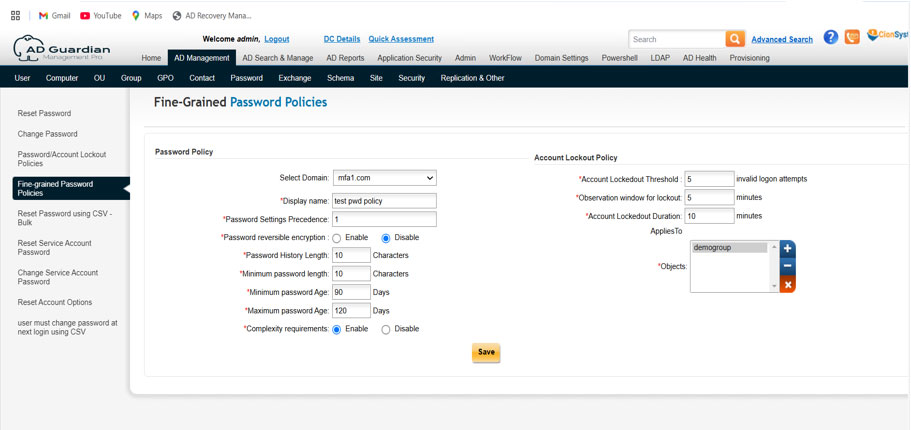
- Fill out the form and click on save button.
Using the Active Directory Administrative Center (ADAC)
1. Open ADAC: Access the Active Directory Administrative Center from the Windows Administrative Tools.
2. Navigate to Password Settings Container: In the ADAC, under your domain, locate the ‘System’ container and select ‘Password Settings Container.’
3. Create a New Password Settings Object (PSO): Right-click on the ‘Password Settings Container,’ select ‘New,’ and then ‘Password Settings.’
4. Configure the PSO: Define parameters such as minimum password length, password complexity requirements, account lockout settings, and password history.
5. Apply the PSO to Users or Groups: After creating the PSO, apply it to specific users or groups by adding them to the ‘Directly Applies To’ attribute of the PSO.
Using PowerShell
1. Install the Active Directory Module: Ensure the Active Directory module for Windows PowerShell is installed.
2. Create a New PSO: Use the `New-ADFineGrainedPasswordPolicy` cmdlet to create a new PSO.
3. Apply the PSO to Users or Groups: Use the `Add-ADFineGrainedPasswordPolicySubject` cmdlet to apply the PSO to specific users or groups.
Limitations of Native Fine-Grained Password Policies
While FGPPs offer enhanced flexibility over default domain policies, they have certain limitations:
– Complexity Settings: The native FGPP interface provides limited options for password complexity.
– Custom Dictionary Lists: FGPPs do not support custom dictionaries to block specific words or phrases.
– Compromised Password Detection: No native mechanism prevents the use of compromised passwords.
– Regulatory Compliance: FGPPs lack predefined templates for compliance with specific regulations.
– Reporting and User Feedback: Native FGPPs do not offer advanced reporting or user feedback capabilities.
Enhancing Password Protection in Active Directory
To address the limitations of native FGPPs, organizations can implement additional measures to enhance password protection:
– Microsoft Entra Password Protection: Helps prevent the use of weak or compromised passwords by enforcing both global and custom banned password lists.
How CionSystems Can Help
CionSystems offers comprehensive solutions to enhance Active Directory security and management:
– AD Guardian: Provides real-time monitoring and alerts for changes in Active Directory.
– Self-Service Password Reset (SSPR): Enables users to reset their passwords securely without administrator intervention.
– Advanced Reporting: Offers deep visibility into the Active Directory environment with extensive reporting capabilities.
– Multi-Factor Authentication (MFA): Enhances login security by requiring multiple forms of verification.
– Disaster Recovery: Provides tools for quick recovery of Active Directory objects and attributes, ensuring business continuity in case of accidental changes or breaches.



